how to log a data breach
You can usually also log out those. Most data breaches involve hacked email accounts and.

Data Breach Response Times Trends And Tips
Data loss a mystery.

. When to report a data breach under GDPR. Responding to a personal data breach We have in place a process to assess the likely risk to individuals as a result of a breach. Make sure the new password is secure.
Overview of the upcoming new breach notification web-forms. Doing it right has moved beyond human capacity. The only email encryption provider you need.
Review logs to determine who had access to the data at the time of the breach. One of the best ways to check if you have been hacked is to enter your email into a number of data breach websites that track breaches and. Code42 Delivers Faster More Comprehensive Responses to Insider Risk.
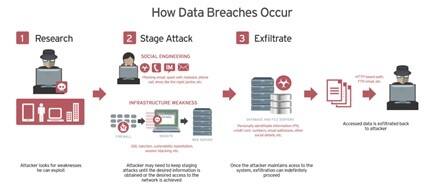
Sometimes a data breach involves financial information including credit card numbers or bank account information. Check data breach websites. Your first priority at this point in time is to isolate the affected system s to prevent.
Answer- select Dept count SSN from from EMP group by Dept. Doing it right has moved beyond human capacity. For a security incident.
Take steps so it doesnt happen. Code42 Delivers Faster More Comprehensive Responses to Insider Risk. Set up a fraud alert or credit freeze.
Ad Secure your enterprise. Discover the core of identity security. Find out which level is responsible for the bulk of the work that has been completed both.
A data breach occurs when sensitive data is copied transmitted viewed stolen or accessed by an unauthorized individual. To prepare for a data breach event policies actions and tools can be put in place to lay out a plan for detecting and containing an. Technically a data breach is a violation of security protocol for an organization or individual in which confidential information is copied.
Ad Discover How To Easily Efficiently Spot Unusual Data Behavior To Protect Your Business. Analyzing logs is the primary way of doing forensics and properly managed logs can also be used as evidence in a court of law for prosecution purposes. Credit and financial theft is the biggest target for identity thieves.
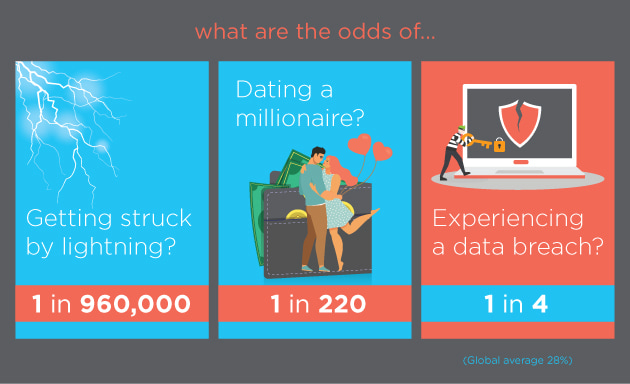
Freeze Your Credit. A data breach is a security violation or incident that leads to the theft of sensitive or critical data or its exposure to an unauthorized party. From 25 May 2018 the General Data Protection Regulation GDPR.
According to the GDPR legislation an organization must report a data breach to a data protection authority DPA also known as a. The breach can be intentional or accidental. 14 hours agoSANTA BARBARA Calif The County of Santa Barbara Department of Behavioral Wellness has experienced a breach in medical record information.
Data Breach Incident Log Template. After a data breach youll want to set up a few fraud prevention safeguards to make. Discover the core of identity security.
An email data breach can happen when there are security issues with an email. Easy-to-use interface privacy protection. The log should describe the incident itself the cause.
Data breacheswhether nefariously intentional or innocently accidentalopen people up to identity theft invasion of privacy and costly financial losses. Summary of Breach Notification Form Changes. This data breach response plan response plan sets out procedures.
Be sure to log into the affected accounts to change your password. We have a process to inform affected individuals about a. Many data breaches will affect your passwords even if it also affects other data.
Dont wipe and re-install your systems yet Do follow your incident response plan. If your Social Security number or financial information was part of a data breach freezing your credit will restrict access to it which makes it challenging for. These incidents can be intentional such as a.
Move quickly to secure your systems and fix vulnerabilities that may have caused the breach. Meaning cybercriminals can gain access to your information through an organisation website. You should act on this type of breach as soon as.
Implement tools services and policies. Discover the core of identity security. The only thing worse than a data breach is multiple data breaches.
Ad Discover How To Easily Efficiently Spot Unusual Data Behavior To Protect Your Business. GDPR requires all firms to keep a log of any and all breaches even the smallest incidents should be recorded. Some online services allow you to view what devices have recently used your login details and any recent transactions.
Ad We protect your data activity and privacy with state-of-the-art security and technology. A data breach is when your personal data is accessed copied or changed by someone without your permission. Review your account security settings.
If your name and phone number were part of a data breach attackers can use it to try to log into your account. Ad Secure your enterprise. The log should describe the.

Data Breach Infographic Data Breach Shocking Facts Infographic

Handling Data Breaches In Your Business Privacy Policies

Onelogin Businesses Vulnerable To Data Breaches By Ex Employees Data Breach Data Vulnerability
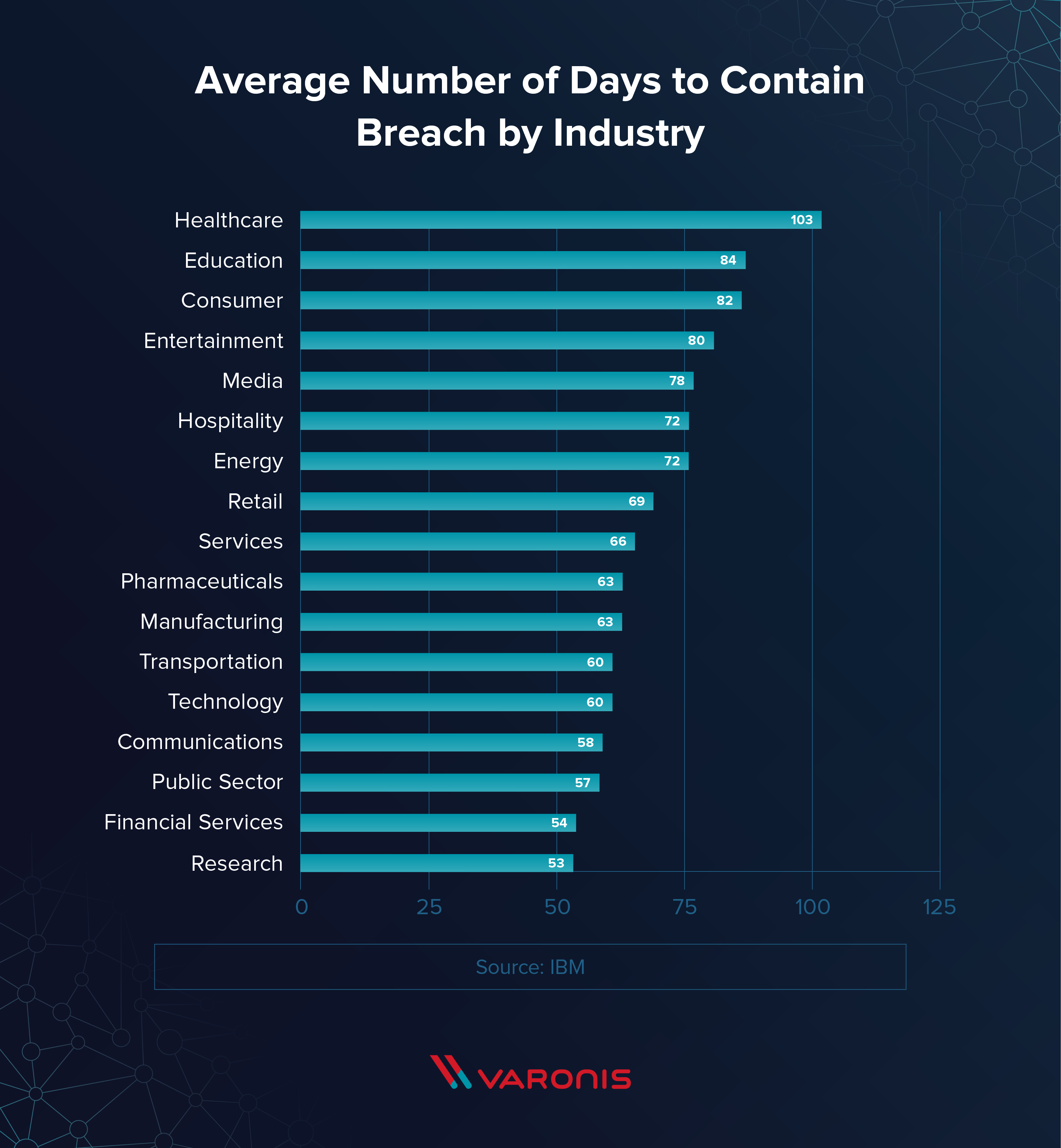
Data Breach Response Times Trends And Tips
6 Steps To Developing A Data Breach Response Plan Spectral

7 Key Steps To Investigate A Data Breach With Checklist Ekran System
6 Steps To Developing A Data Breach Response Plan Spectral

Gdpr 4 Passi Verso La Conformita 2 4 Key4biz Lezioni Di Informatica Sicurezza Informatica Conformismo
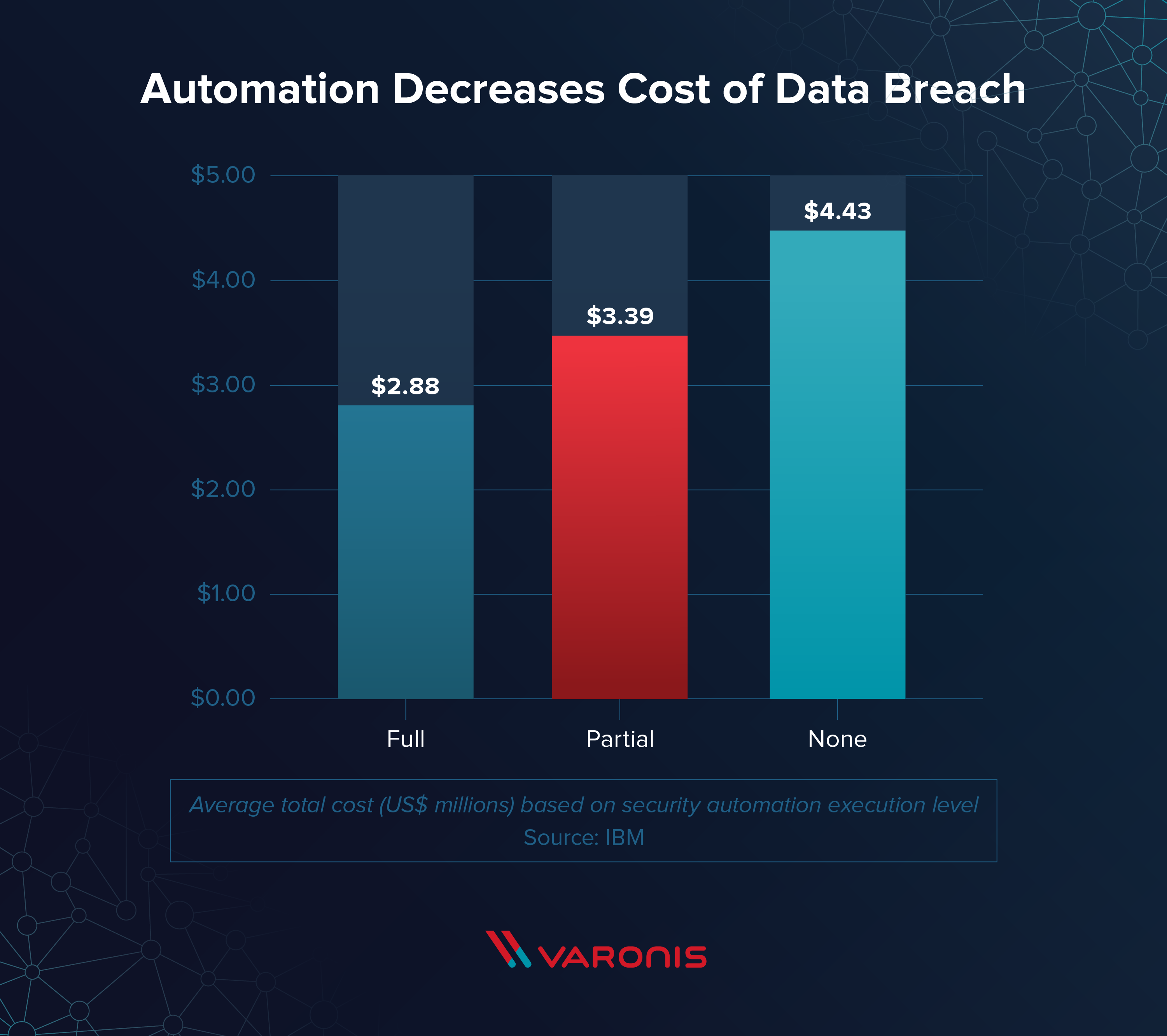
Data Breach Response Times Trends And Tips

How To Deal With A Data Breach Of Your Personal Info Privacy Policies

7 Key Steps To Investigate A Data Breach With Checklist Ekran System

Common Data Breach Causes Cyber Security Awareness Infographic Marketing Data Breach

6 Steps To Developing A Data Breach Response Plan Spectral

How To Write Gdpr Compliant Data Breach Notification Letters Privacy Policies

Data Breaches In The Financial Service Industry Rise In 2016 Fintech Security Data Breach Infographic Cyber Security

How To Write Gdpr Compliant Data Breach Notification Letters Privacy Policies